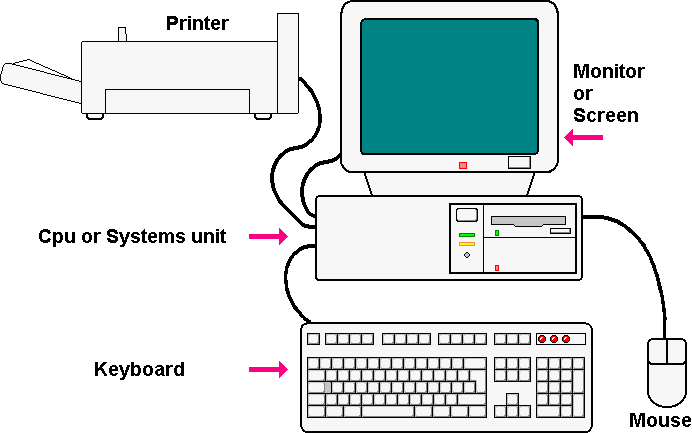
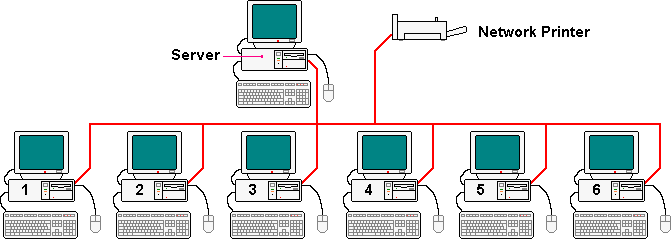
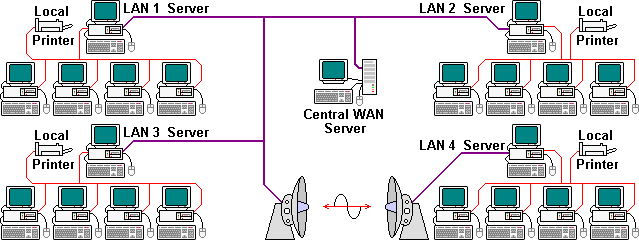
| |
The Simplest Possible Tutorial...
Understanding How Computers Work
|
|---|
|
This tutorial was developed to help Chris Bell and Robert
Wright to come to terms with, and be more confident in handling, their
personal computers. However I believe that there are others that can
benefit from a gentle introduction to what may seem to be a technical
subject.
|
|
Any 'new' technical words that are introduced in the body
text, will be highlighted at their first use, clicking on the
highlighted word will take you directly to the entry in the glossary
for the word concerned. Entries in the menu at top left of this page
will take you to a sub page describing the topic.
|
I have heard people say that they are frightened of doing
damage by pressing the 'wrong' buttons. There are a few occasions when
pressing a button at an inappropriate time will cause you to lose some
data or disrupt a
program
application, but
these are few and far between. If we take the right steps in the first
place then those events that do occur will be of minor consequence as the situation will be a recoverable one.
|
|
|---|